Top 6 Home Cybersecurity Techniques for Remote Workers

Invisible but deadly – In just a few weeks, the sudden emergence in December 2019 and subsequent global spread of Coronavirus (COVID-19) changed the world as we know it. Social distancing techniques were encouraged in the white-collar world, and governments worldwide urged employees to work from home wherever possible.
On the surface, the power of the Internet seemed to make it relatively simple for many workers to carry out their regular desk-job duties from the dining room table or the comfort of their couch.
Conceivably, they could generate roughly the same output in such a way without causing too much disruption to your clients, investors, partners, and business. However, moving at short notice from a secure and trusted office environment to remote working created cybersecurity risks because most businesses were caught off guard and had no tried and tested work-from-home policy in place.
Fast forward, and working from home is now the new normal. This post will cover the concept of cybersecurity, different types of cybersecurity issues, some practices remote workers can implement to improve cybersecurity, and how Zsah’s trustworthy service can help keep your organisation secure.
What is cybersecurity?
Cybersecurity Threats to Remote Workers
Cybersecurity risks are, of course, always rife, and a constant threat to businesses. However, as more and more of your workforce starts working from home, new challenges are presented. Without proper policies, procedures, training, and defence systems in place, not only can your remote workers have their own privacy jeopardised, but company security can come under threat too.
Some Examples of Cybersecurity Issues
Phishing Scams
Opportunist cybercriminals used the coronavirus to launch attacks targeting remote workers. Experts at the NCSC – the cyber arm of GCHQ – spotted a range of scams and cybersecurity threats that took advantage of the outbreak, with COVID-19-related phishing scams emerging as a particular threat.
Such scams involved cybercriminals sending emails claiming to be from legitimate organisations – or even your company’s own office – with information about the coronavirus. The email message asked your employee to click on a link or open an attachment to access the information.
If the worker clicked on the attachment or embedded link, they triggered malicious software (malware) download. For example, this malware could allow the criminal to take control of the worker’s device, log their keystrokes, install ransomware, or access private or company data.
“The NCSC has seen an increase in the registration of webpages relating to the coronavirus suggesting that cybercriminals are likely to be taking advantage of the outbreak.
These attacks are versatile and can be conducted through various media, adapted to different sectors and monetised via multiple means, including ransomware, credential theft, bitcoin or fraud.
Continued global susceptibility to phishing will probably make this approach a persistent and attractive technique for cybercriminals. Moreover, if the outbreak intensifies, it is highly likely that the volume of such attacks will rise.” said the UK National Cyber Security Centre (NCSC) in a statement issued in March 2020.
What Do Phishing Emails Look Like?
COVID-19-themed phishing emails can take many forms – including workplace policy emails.
Such emails are “dressed up” to appear as if they come from inside your company and contain information or instructions on what workers should do with regards to the outbreak. One phishing email targeting workplace email accounts, for example, was found to contain a malicious link supposedly to a “Communicable Disease Management Policy” issued by HR departments. By clicking on the link, however, the worker triggers a malware download.
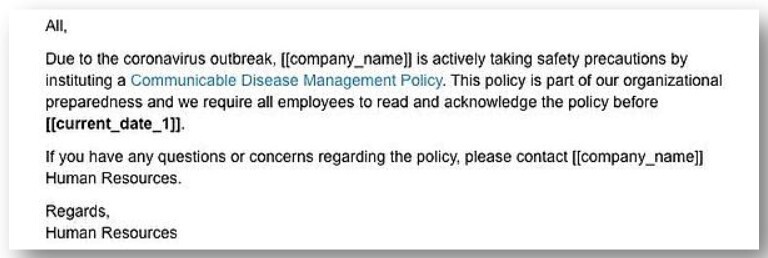
(Image source: norton.com)
Across the pond, cybercriminals have also gone down the route of impersonating the US Centers for Disease Control (CDC). The message advises recipients to click on a malicious link purporting to list coronavirus cases in their area.
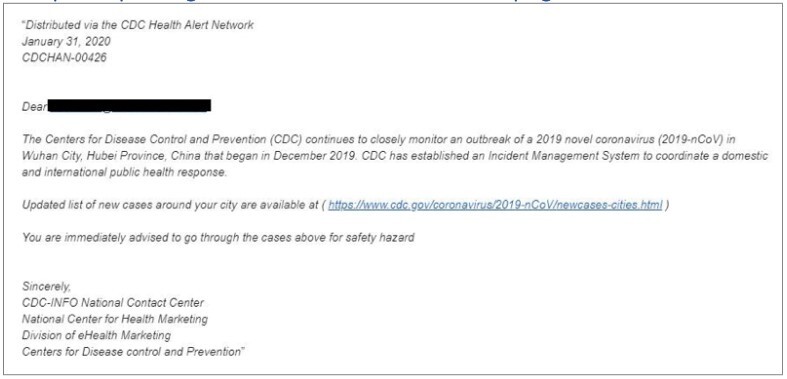
(Image source: norton.com)
Other fraudulent health advice emails were also in circulation. They purported to be from a medical institution like the World Health Organization (WHO) and were designed to trick recipients into opening a malicious attachment.
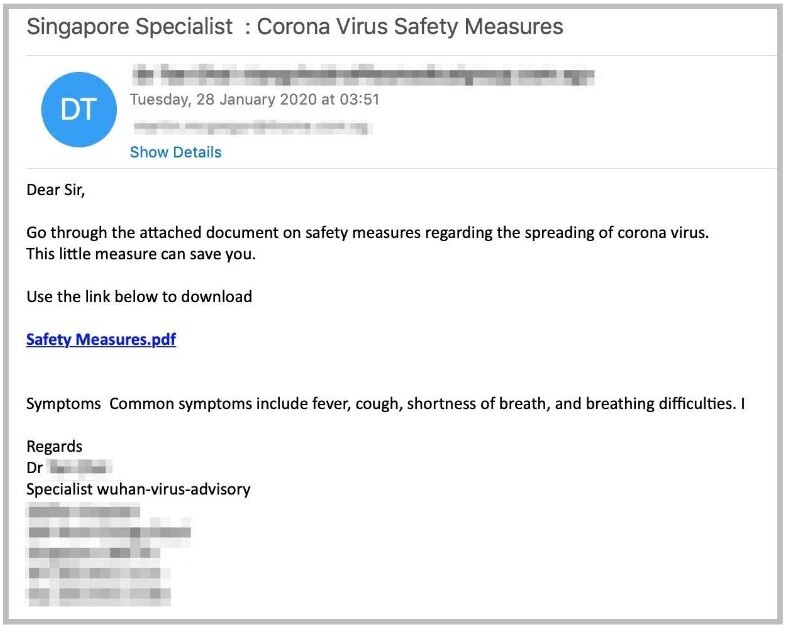
(Image source: norton.com)
Still more targeted workers from specific sectors to increase the likelihood of success. Researchers at Proofpoint, for instance, found that attackers had been sending an email with a malicious Microsoft Word document attached to workers in the shipping industry. The document sought to exploit a Microsoft Office vulnerability and install AZORult – an information-stealing malware – on the user’s device.
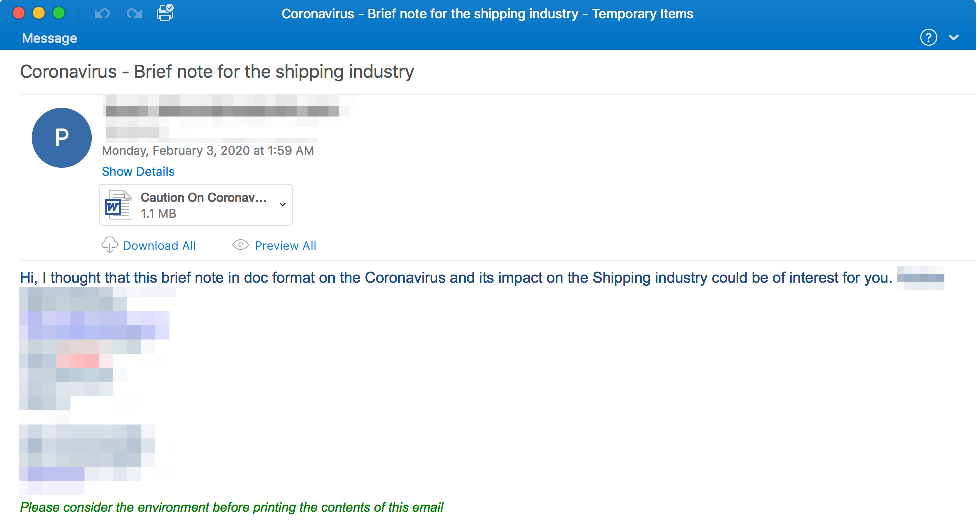
(Image source: proofpoint.com)
Personal Devices
Working from home means that many of your employees have to rely on their personal devices – computers, smartphones and tablets, plus any internet access hardware – to complete work tasks.
The trouble here is that these usually lack the tools already built into your business office networks, such as strong antivirus software, customised firewalls, and automatic online backup solutions. This creates a significant cybersecurity risk as it increases the likelihood of malware finding its way onto devices and both personal and work-related data being breached.
An alternative option is for your company to provide new devices to your employees. In this way, you could ensure that they have all the necessary defence mechanisms installed – though this may of course be a prohibitively expensive strategy to deploy, especially during times of crisis.
Unsecured Wi-Fi Networks
Since the whole idea behind remote working during the coronavirus pandemic is to promote social distancing, your employees should be aiming to avoid co-working and shared-space environments while out of the office. However, it may be the case that some team members may either choose or be forced to use unsecured public Wi-Fi networks from time to time. Unfortunately, these are prime spots for malicious actors to spy on internet traffic and steal confidential information.
An attacker could potentially position him/herself between the worker and the connection point – so, instead of talking directly with the hotspot, all information sent over the internet is intercepted by the hacker, including emails, credit card information, and security credentials to your business network. In addition, an attacker could use an unsecured Wi-Fi connection to distribute malware.
Most employees are working from home, however, where they should be able to secure their Wi-Fi. Most home Wi-Fi systems are well-secured these days, though some older installations may not be. As is the case with public networks, with an insecure home connection, an attacker in the near vicinity can potentially snoop internet traffic and distribute malware.
What are the Home Cybersecurity Techniques for Remote Workers?
While you, as a company, refine your work-from-home policies for your remote workforce, cybersecurity will always be one of the most important items in the programme.
There are several simple, time-tested, yet effective cybersecurity measures your remote workers can take to protect themselves and your business immediately while working from home.
Technique #1: Recognise and Avoid Phishing Emails
The first thing here is to make sure your remote workers are aware of the growing threat.
Why?
With the rise in the number of people working from home, cybercriminals are actively trying to cash in on the trend. As such, phishing emails – as well as voicemails (vishing) and SMS text messages (smishing) – are targeting remote workers looking to steal their personal information or gain access to company accounts.
Ransomware has been particularly egregious. For example, US victims were forced to pay an estimated $350 million to criminals in 2020, according to a ransomware task force report by the global security group the Institute for Security and Technology.
(Image source: IST)
Communicate with your workforce so they are aware of these risks and are alert to the potential cybersecurity threats presented by any message that arrives in their inbox.
Workers must be told not to follow any links, click on any attachments, or reply to any messages until they are 100% certain that the sender is genuine.
Tips: Checklist for spotting fraudulent phishing emails
- Look out for poor grammar, spelling and punctuation, and other signs of poor quality (such as design) that you wouldn’t normally expect from the organisation the email is supposed to have come from.
- Beware of requests for personal or company information, as this is precisely what cybercriminals are after. Legitimate agencies won’t ask for login credentials, credit card information, or other such data. Do not respond.
- Look out for veiled threats that ask you to “act urgently”. Phishing emails often demand immediate action – “send these details within 24 hours” or “click here immediately”. The goal is either to get you to provide personal or company information, or otherwise trigger a malware download.
- Beware of generic greetings like “Sir/Madam”, “Colleague”, “Friend”, or “All”. This is a clear sign that the sender does not know you, and may indicate a phishing scam.
- Check any links provided by hovering your mouse cursor (without clicking) over the URL to see where it leads. Sometimes, it will be clear that the website is not genuine – though bear in mind that cybercriminals will create links that closely resemble legitimate addresses. If you are in any doubt at all, do not click.
Technique #2: Secure Home Routers
Hackers will be on the lookout for remote workers with vulnerable home networks.
Why?
The harder it is for a cybercriminal to breach your workers’ defenses, however, the less likely they are to bother trying and will move on to alternative targets.
Tips: Steps to firm up the security of your wireless routers
- Pick a new username (many routers ship with the same default username from the manufacturer, such as “admin”) along with a complex password that contains letters, numbers and symbols.
- Ensure firmware updates from the manufacturer are routinely installed so that security vulnerabilities can be patched.
- Use the highest levels of encryption available – such as WPA2 or WPA3.
- Restrict inbound and outbound traffic.
- Disable all unused services.
Technique #3: Set Up Firewalls
It’s likely that your remote workers’ devices and routers will have built-in firewalls, which create a barrier of defence between the device and the internet by closing ports to communication.
Why?
Firewalls help prevent malicious programs entering and can stop data leaking from devices. Ensure that your remote workers’ enable these built-in firewalls if they’re present.
If any device being used for work doesn’t have a built-in firewall, the worker must install one from a third-party provider immediately. Even if they do, however, an additional third-party firewall can offer added protection and you should encourage your remote workforce to install one.
Tips: Reliable firewall options
Some good free and paid firewall options for 2021 can be found here.
Technique #4: Install Antivirus Software
While we may be waiting 12 months or possibly much longer for a coronavirus vaccine, strong antivirus software that will protect your remote workers against malware already exists – and they should use it.
Why?
While firewalls act as a good first line of defence, they are not perfect, and installing antivirus software as well as an additional firewall increases your workers’ chances of keeping their equipment malware-free.

(Image source: uk.pcmag.com)
(Image source: uk.pcmag.com)
Technique #5: Use a Virtual Private Network (VPN)
Using a VPN is a simple yet hugely effective home cybersecurity technique for remote workers.
Why?
A VPN will encrypt all traffic going to and from your employees’ devices, rendering it unreadable to anyone who should try to intercept it, thereby keeping your company information safe.
Tips: Create a personal tunnel for internet traffic
By creating a persona and encrypted tunnel for internet traffic to go through that no one else can access, you can effectively help secure your information. It’s important to note, however, that using a VPN can slow down internet speeds, so it’s important to choose one known not only for its high security, but speed and reliability as well.
From network security monitoring and management to centralized policy-based email encryption solutions, to threat analytics and detection, Zsah is now offering a discounted cloud and SaaS-based cyber-security consultancy services to help keep your organisation secure. Click to learn more.
(Image source: wpbeginner.com)
Comapritech provides a list of robust VPNs for remote workers in 2021, which can be found here.
Technique #6: Use Strong Passwords
Last, but by no means least, is to ensure all accounts are protected with strong passwords.
Why?
According to a 2021 IBM report, stolen credentials are the most common cause of data breaches, making employee passwords one of the biggest ongoing threats to corporate security – whether the employees using them are remote working or not.
Depending on your business, the number of applications your employees may need to use to perform their duties can reach dozens if not hundreds. Effective identity management is therefore crucial. Strong, unique passwords should be used for every application – but password reuse is by no means uncommon. The IBM report notes that “82% of individuals surveyed admitting they reuse passwords across accounts, compromised credentials represent both a leading cause and effect of data breaches, creating a compounding risk for businesses.”
This means that if a cybercriminal were to compromise one password, they could use credential stuffing techniques to try and log in to other online accounts and steal any data they find.
Tips: The use of password managers
A robust password policy must therefore be enforced. It is of course almost impossible for employees to remember a long list of strong passwords with strings of random letters, numbers and symbols. As such, the use of password managers which create, remember and autofill passwords should be endorsed.
(Image source: uk.pcmag.com)
Zsah’s Trustworthy Enterprise Cybersecurity Services
Like it or not, we’re facing a new world of remote working for the foreseeable future. The coronavirus forced enterprises to rethink the way they do business and create robust new policies for remote workers.
It is imperative that your business’s cybersecurity is not thrown into jeopardy by similar risks in future. While you hopefully have a strong work-from-home cybersecurity plan, communicating the above cybersecurity techniques to your workforce so they can start implementing them mitigates the risk.
Even so, it is now more crucial than ever to work with a high-quality cybersecurity services provider like Zsah to keep your organisation secure.
Zsah's security experts can help you boost cyber resiliency and reduce risk by assessing your infrastructure and policies based on your business needs. If you need to implement a work from home strategy, our technical consultants are here to get you up and running in the shortest possible time to minimise the impact on your business.
Get in touch today for more information.



Thanks for really in-depth blog on cybersecurity, it covers everything you need to know. Can’t emphasize more on its importance in this generation, considering the novel hacking techniques cybercriminals have devised. Managed IT service providers help tackle this issue in a more structured and proactive manner for businesses, securing all your data and employees from scams and threats.